Featured
Table of Contents
- – Vpns And Vpn Technologies - How Ipsec Works
- – What Is Internet Protocol Security (Ipsec)?
- – Site To Site Ipsec Vpn Phase-1 And Phase-2 Tro...
- – Ipsec Explained: What It Is And How It Works
- – Using Sauce Ipsec Proxy
- – How Ipsec Works, It's Components And Purpose
- – Difference Between Ipsec And Ssl
- – Ipsec Vpn
- – What Is Ipsec And How It Works
- – Difference Between Ipsec And Ssl
Vpns And Vpn Technologies - How Ipsec Works
IPsec (Internet Procedure Security) is a structure that helps us to protect IP traffic on the network layer. Why? because the IP protocol itself does not have any security includes at all. IPsec can secure our traffic with the following features:: by securing our data, no one other than the sender and receiver will be able to read our data.

By computing a hash worth, the sender and receiver will have the ability to examine if modifications have actually been made to the packet.: the sender and receiver will verify each other to make certain that we are really talking with the gadget we plan to.: even if a package is encrypted and verified, an aggressor could try to record these packets and send them once again.
What Is Internet Protocol Security (Ipsec)?
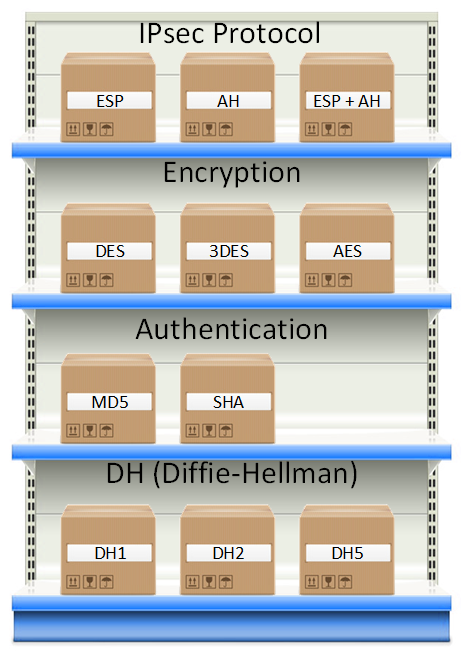
As a structure, IPsec uses a range of protocols to execute the functions I explained above. Here's an overview: Do not fret about all the boxes you see in the image above, we will cover each of those. To provide you an example, for encryption we can choose if we wish to use DES, 3DES or AES.
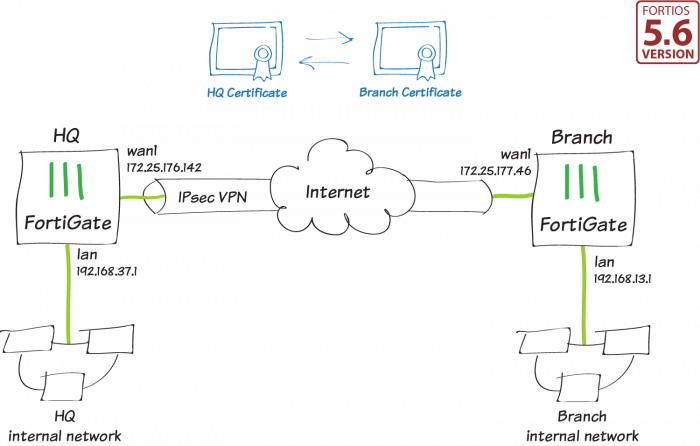
In this lesson I will begin with an overview and after that we will take a better take a look at each of the elements. Prior to we can protect any IP packages, we require two IPsec peers that build the IPsec tunnel. To develop an IPsec tunnel, we utilize a protocol called.
Site To Site Ipsec Vpn Phase-1 And Phase-2 Troubleshooting ...
In this stage, an session is established. This is likewise called the or tunnel. The collection of parameters that the two devices will utilize is called a. Here's an example of 2 routers that have actually established the IKE phase 1 tunnel: The IKE phase 1 tunnel is only utilized for.
Here's a photo of our 2 routers that finished IKE phase 2: Once IKE stage 2 is completed, we have an IKE stage 2 tunnel (or IPsec tunnel) that we can utilize to safeguard our user data. This user information will be sent through the IKE stage 2 tunnel: IKE develops the tunnels for us but it doesn't authenticate or secure user data.
Ipsec Explained: What It Is And How It Works
I will explain these two modes in detail later on in this lesson. The entire process of IPsec consists of 5 steps:: something has to activate the production of our tunnels. When you set up IPsec on a router, you use an access-list to tell the router what data to secure.
Whatever I describe below uses to IKEv1. The primary purpose of IKE stage 1 is to develop a secure tunnel that we can utilize for IKE phase 2. We can break down phase 1 in 3 easy actions: The peer that has traffic that needs to be safeguarded will initiate the IKE phase 1 negotiation.
Using Sauce Ipsec Proxy
: each peer needs to prove who he is. 2 typically utilized choices are a pre-shared secret or digital certificates.: the DH group figures out the strength of the secret that is utilized in the key exchange procedure. The greater group numbers are more secure but take longer to calculate.
The last action is that the two peers will verify each other using the authentication approach that they concurred upon on in the settlement. When the authentication achieves success, we have actually finished IKE phase 1. The end result is a IKE phase 1 tunnel (aka ISAKMP tunnel) which is bidirectional.
How Ipsec Works, It's Components And Purpose
This is a proposal for the security association. Above you can see that the initiator utilizes IP address 192. 168.12. 1 and is sending out a proposal to responder (peer we want to connect to) 192. 168.12. 2. IKE utilizes for this. In the output above you can see an initiator, this is a special worth that determines this security association.
0) which we are utilizing main mode. The domain of interpretation is IPsec and this is the first proposal. In the you can discover the qualities that we want to use for this security association. When the responder gets the first message from the initiator, it will reply. This message is used to inform the initiator that we agree upon the characteristics in the change payload.
Difference Between Ipsec And Ssl
Because our peers settle on the security association to utilize, the initiator will begin the Diffie Hellman essential exchange. In the output above you can see the payload for the crucial exchange and the nonce. The responder will likewise send out his/her Diffie Hellman nonces to the initiator, our two peers can now determine the Diffie Hellman shared secret.
These two are utilized for identification and authentication of each peer. The initiator begins. And above we have the 6th message from the responder with its recognition and authentication information. IKEv1 main mode has actually now completed and we can continue with IKE phase 2. Prior to we continue with phase 2, let me reveal you aggressive mode.
Ipsec Vpn
You can see the change payload with the security association characteristics, DH nonces and the identification (in clear text) in this single message. The responder now has whatever in needs to create the DH shared essential and sends some nonces to the initiator so that it can likewise determine the DH shared key.
Both peers have whatever they need, the last message from the initiator is a hash that is utilized for authentication. Our IKE stage 1 tunnel is now up and running and we are all set to continue with IKE phase 2. The IKE stage 2 tunnel (IPsec tunnel) will be actually used to safeguard user information.
What Is Ipsec And How It Works
It protects the IP packet by calculating a hash worth over practically all fields in the IP header. The fields it omits are the ones that can be changed in transit (TTL and header checksum). Let's begin with transport mode Transportation mode is basic, it just includes an AH header after the IP header.
With tunnel mode we add a brand-new IP header on top of the initial IP package. This might be helpful when you are using private IP addresses and you require to tunnel your traffic over the Internet.
Difference Between Ipsec And Ssl
Our transportation layer (TCP for example) and payload will be encrypted. It also provides authentication however unlike AH, it's not for the entire IP packet. Here's what it looks like in wireshark: Above you can see the original IP packet which we are using ESP. The IP header is in cleartext but whatever else is encrypted.
The original IP header is now likewise encrypted. Here's what it appears like in wireshark: The output of the capture is above is similar to what you have seen in transport mode. The only difference is that this is a brand-new IP header, you don't get to see the original IP header.
Table of Contents
- – Vpns And Vpn Technologies - How Ipsec Works
- – What Is Internet Protocol Security (Ipsec)?
- – Site To Site Ipsec Vpn Phase-1 And Phase-2 Tro...
- – Ipsec Explained: What It Is And How It Works
- – Using Sauce Ipsec Proxy
- – How Ipsec Works, It's Components And Purpose
- – Difference Between Ipsec And Ssl
- – Ipsec Vpn
- – What Is Ipsec And How It Works
- – Difference Between Ipsec And Ssl
Latest Posts
7 Best Vpns For Business In 2023 And Some To Avoid
Best Phone Vpn In 2023
Vpn Not Working On Windows - Common Errors & Fixes
More
Latest Posts
7 Best Vpns For Business In 2023 And Some To Avoid
Best Phone Vpn In 2023
Vpn Not Working On Windows - Common Errors & Fixes